random jigs from a K12 IT professional
tls.pagePosted on July 8th, 2025 by Jon I'm excited to finally get to the blog-post phase of a project I've been working on for a while: tls.page. It's a web-based tool designed to simplify obtaining TLS certificates in a particular set of use cases. The Challenge of TLS for Internal and IP-Based Services
TLS is a cornerstone of web security. For public-facing websites, acquiring a TLS certificate has become a streamlined process, often requiring no configuration at all thanks to built-in ACME support. However, the situation is often more complex for services not directly exposed to the public internet. This includes development servers, internal admin interfaces, IoT devices, or services typically accessed via an IP address. In these scenarios, self-signed certificates are a common workaround. While they provide encryption, they produce browser trust warnings and can complicate the distribution of trust to clients and users. tls.page aims to offer an alternative by making it easier to obtain publicly-trusted certificates for these scenarios. How tls.page Works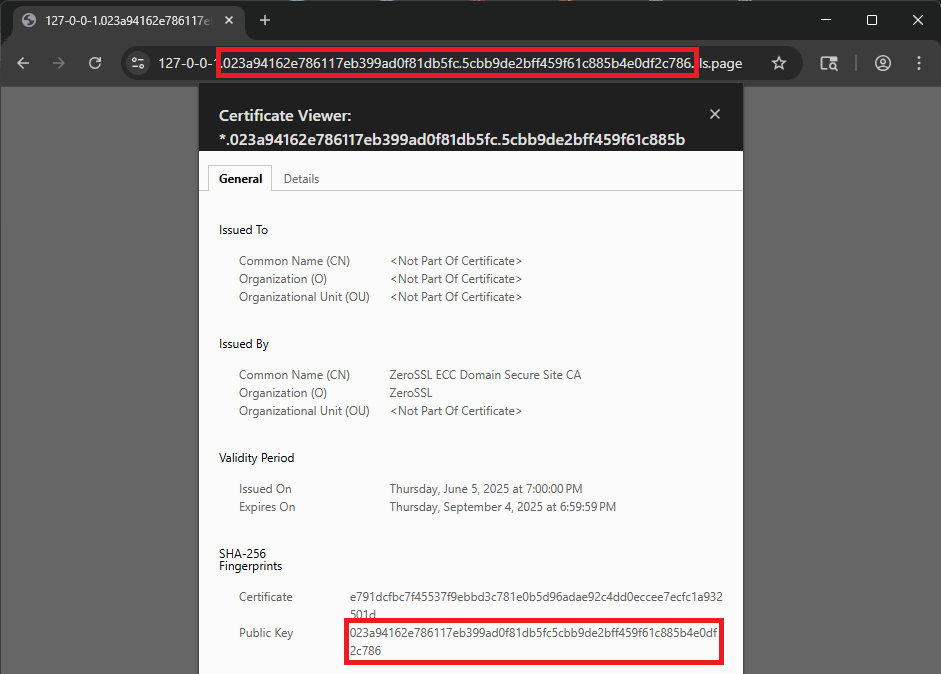
The fundamental concept of tls.page is to link the domain name directly to the cryptographic identity of a server - specifically the hash (also called fingerprint) of it's public key. Upon generating a key pair, tls.page utilizes the fingerprint of the public key to formulate a unique domain name. For instance, if a public key's SHA-256 fingerprint is "023a94162e786117eb399ad0f81db5fc5cbb9de2bff459f61c885b4e0df2c786", tls.page will issue a wildcard certificate for "*.023a94162e786117eb399ad0f81db5fc.5cbb9de2bff459f61c885b4e0df2c786.tls.page". The fingerprint is hex-encoded, and split in half to comply with the 63-character limit for DNS labels. DNS for the domain is configured such that there is a subdomain for any possible IPv4 or IPv6 address. For example:
Security Considerations
Using tls.page implies a shift in the security verification model. Users are unlikely to recognize or
memorize a lengthy, fingerprint-based domain such as
However, in many of the intended use cases for tls.page, direct URL entry by users is not typical. Instead, users might be:
In these situations, the primary security assurance comes from the authenticity of the link itself. If you trust the source of the link, you can trust you're connecting to the right place. Put another way, tls.page enables key-pinned-links, where the domain name intrinsically vouches for the public key. For scenarios involving manual URL entry from a display (e.g., an IoT device), these long domains can be impractical. However, integration with a URL shortening service could potentially address this. Key Featurestls.page incorporates several features to enhance its utility and reliability:
Why I Built This
tls.page started as a personal project to address a recurring need I had. I wanted quick, trusted TLS certificates for internal projects, development servers, or devices on my local network. Existing solutions felt too cumbersome, and I wound up with a lot of things using self-signed certificates. Developing tls.page was an interesting challenge, and it felt like something that ought to exist. Exploring tls.pageIf this functionality seems relevant to your work or projects, I encourage you to explore tls.page. The website, API, and client are available for use. For those interested in the underlying implementation, the source code is accessible on GitHub. Feedback is always welcome via the comments below or github issues. I did kind of a brain-dump, then asked Google Gemini to structure it into a blog post, then re-wrote a lot of it. Depending on your definition this might be AI generated content. |
|
8 CommentsLeave a Comment
To reduce spam comments must be manually approved (you won't see them right away)
Comments containing links will have them removed Leave a Reply |
|
Hi, how have you been lately?
It's been a good day; rainy. I like rain. Me and a friend went to stare at a stream. I appreciate you letting me know you checked out my site. I hope you have a wonderful day.
Hi
Hello. Here for the tech, or just poking around the independent corners of the internet?
Hello
Hello 🙂
How are you?
I'm doing really well. I just got over being sick (there is nothing like feeling bad to make you appreciate just feeling normal). Also I'm loving all this snow. It's so beautiful. I might post some of my snow pictures on here later.